Listen to this blog
When most people hear the word hacker, it often comes with a negative connotation attached with it. We picture a criminal sitting in the dark wearing a hoodie hunched over a keyboard, trying to steal credit card numbers. I get it. But what if I told you the truth is far more interesting, in fact, important than that?
My own journey into the world of hacking did not start with a grand plan, but just with simple curiosity. My father owned a video studio in the 90s where I got access to the old 286, 386 computers with Windows 3.0 and DOS. Helping dad with animating gigs using DOS Animator Pro helped me grow my interest in computers and their mechanisms.
Being a kid who loved fiddling with computers from as early as my school days, I had told my friends that I knew how to hack. Shocked by that, a kid from a neighbouring class accused me of being a fake until I hacked his computer to prove him wrong. That’s how our friendship story and my fame to being a mastermind of computers began. That little stint of mine didn’t cause any trouble but gave me a firsthand experience at knowing computers better.
What It Means to Be a Hacker
Hacking, according to me, is not a single act but a mindset. It requires one to use technology in creative ways. The main difference between a good hacker (‘White Hat’) and a bad one (‘Black Hat’) is not the skill, but the intention. Ethical or White Hat hackers use their skills to identify vulnerabilities and weaknesses, not to exploit them, but to protect against the Black Hats. As a wise colleague of mine once said,
“The only way to defeat a hacker is to think like one.”

- Black hat: Uses hacking skills for illegal or harmful purposes, such as stealing data or breaking into systems for personal gain.
- White hat: Uses the same skills for lawful and often beneficial purposes, such as finding vulnerabilities so they can be fixed.
- Gray hat: Operates in between, sometimes breaking rules or laws but without malicious intent.
The skills of a hacker do not matter as much as their intentions. There is no such thing as a ‘black hat’ or a ‘white hat’ in real life. It all comes down to a choice: will you use your knowledge and skills to steal, or will you use it to protect?
Understanding a Digital Attack
First, let us understand what a digital attack is. It is as simple as you visiting a website, thus giving away a surprising amount of your information. Things like your operating system, browser, and even screen resolution can be collected without you ever realizing it. In the wrong hands, this data can be used for malicious purposes.
What can hackers do? They can use your IP address to scan your computer for ports. Think of these like doors into your system. Every computer has some open doors to let software run, but a malicious hacker can use them to sneak in. Once they have control, they can track your webcam, record your audio, or more. This is just one way data is collected and exploited.
Being a ‘White Hat’
When cyberattacks happen, cybersecurity is necessary, and we are the guardians of it. Wearing a white hat means we can think like a criminal but act with a moral compass. We put on our figurative white hats and use our skills to find vulnerabilities and fix them before the bad guys can exploit them. It’s a constant battle, but it’s one of the most rewarding careers out there.
Methods, like social engineering, are a big part of the game. It’s not about being a tech whiz, but about understanding human psychology. For example, a hacker might call you pretending to be from your bank to get your password. Another tactic is something called a ‘man-in-the-middle’ attack, where a hacker intercepts your communication with a website to steal your data. But as a white hat, you learn to spot these tricks and build stronger defenses.
Attack Cycle and The Defense Blueprint
By understanding the blueprint of an attack, ethical hackers can defend better. A systematic process is followed to do so:
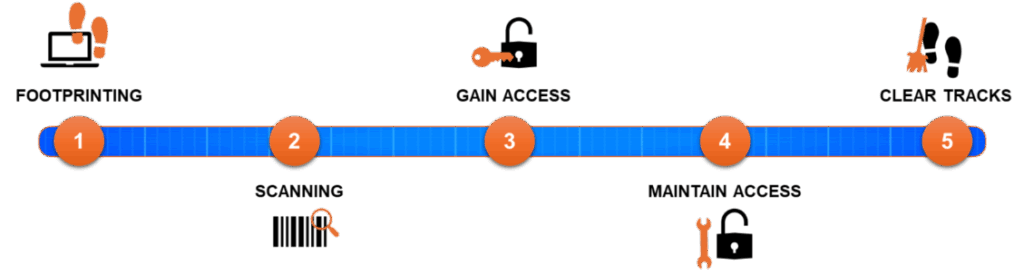
- Reconnaissance (or Footprinting)
This is the intelligence-gathering phase. I once heard about a Black Hat who gained access to a company simply by posing as a pizza delivery guy and observing employee badges and desk setups. This is passive reconnaissance, collecting information without direct interaction. On the other hand, active reconnaissance involves probing the network directly to get a sense of its structure. My own experience has taught me that this is often the most critical phase. The more information you gather, the more effective your subsequent attacks will be.
- Scanning
Once you have identified your target, you begin scanning. This is where we use specialized tools to look for open ports, running services, and other potential entry points. It’s like a burglar checking all the windows and doors of a house to see if any are unlocked.
- Gaining access
This is where actual hacking happens. Based on the information gathered during scanning, hackers choose a specific exploit to gain entry. This could be anything from a known software vulnerability to a misconfigured system.
- Maintaining Access
Hackers do not want to get in and then get locked out. This phase is about establishing a persistent presence. A hacker might install a backdoor or a rootkit where malicious software allows us to return to the system at any time, often undetected.
- Clearing Tracks
The final step is to erase any evidence of the intrusion. This involves deleting or modifying logs and other system files. A skilled black hat hacker will leave no trace, making it incredibly difficult for a company’s security team to figure out what happened, how they got in, and what they took.
Ethical Hacking and Its Demand
The global demand of cybersecurity positions is about 3.5 million in 2025. This has seen a 68% jump from 2020 thus emerging as an in-demand field for growth opportunities across industries.
The career progression path for a cybersecurity specialist can look like:

The top hiring sectors include:

Skills Required for a Career in Cybersecurity
- Certifications
- CEH Certification: The Certified Ethical Hacker credential by EC-Council is globally recognized as the standard for ethical hacking.
- OSCP Certification: The Offensive Security Certified Professional (OSCP) is one of the most respected and challenging penetration testing certifications in cybersecurity.
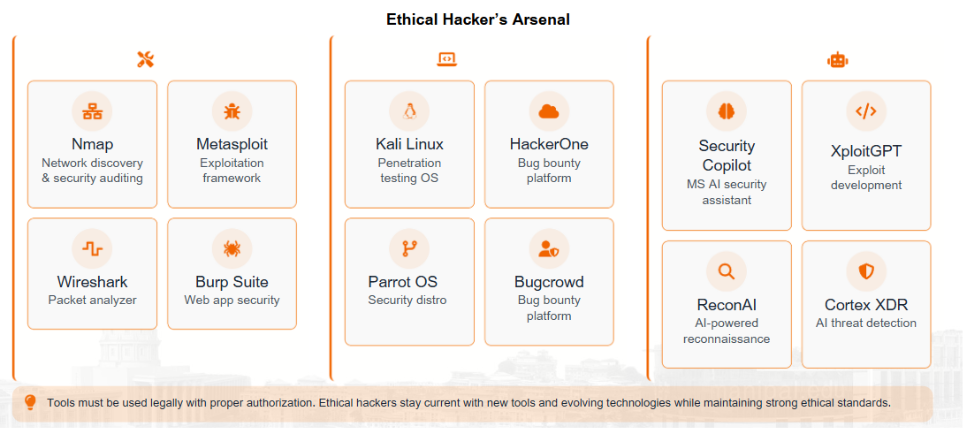
- Tools and platforms
What Your Career Could Look Like
Cybersecurity is an evolving field that is always presenting new challenges. The constant battle between offense and defense means there is no room for complacency. Events like the geopolitical conflicts we see today highlight just how critical our work is. A skilled cybersecurity professional is one of the most valuable assets a company or even a nation can have.
For those serious about this path, an online program can provide the structured learning you need. For example, the MCA from Online Manipal is designed to equip you with the expertise needed to excel. The curriculum includes key concepts like ethical hacking, network security, and cryptography, giving you a comprehensive education to protect digital infrastructures and become a valuable asset in this critical field.
Prepare for your next career milestone with us